Lab 9.1 the Privacy Rights Clearinghouse (PRC) is a nonprofit orga...
Question
Lab 9.1
the Privacy Rights Clearinghouse (PRC) is a nonprofit organization whose goals are to raise consumers’ awareness of how technology affects personal privacy and empower consumers to take action to control their own personal information. The PRC maintains a searchable database of security breaches that impact consumer’s privacy. In this project you will gather information from the PRC website.
1. Open a web browser and enter the URL www.privacyrights.org/ data-breach.
2. The location of content on the Internet may change without warning. If you are no longer able to access the site through the above web address, use a search engine to search for “Privacy Rights Clearinghouse data breachâ€.
3. First spend time reading about the PRC. Click About Us in the toolbar.
4. Scroll down to the content under Mission and Goals and also under
5. Services. Spend a few minutes reading about the PRC.
6. Click your browser’s Back button to return to the previous page.
7. On the Chronology of Data Breaches page scroll down and observe the different breaches listed in chronological order.
8. Now create a customized list of the data that will only list data breaches of educational institutions. Scroll back to the top of the page.
9. Under Select organization type(s), uncheck all organizations except EDU- Educational Institutions.
10. Click GO!.
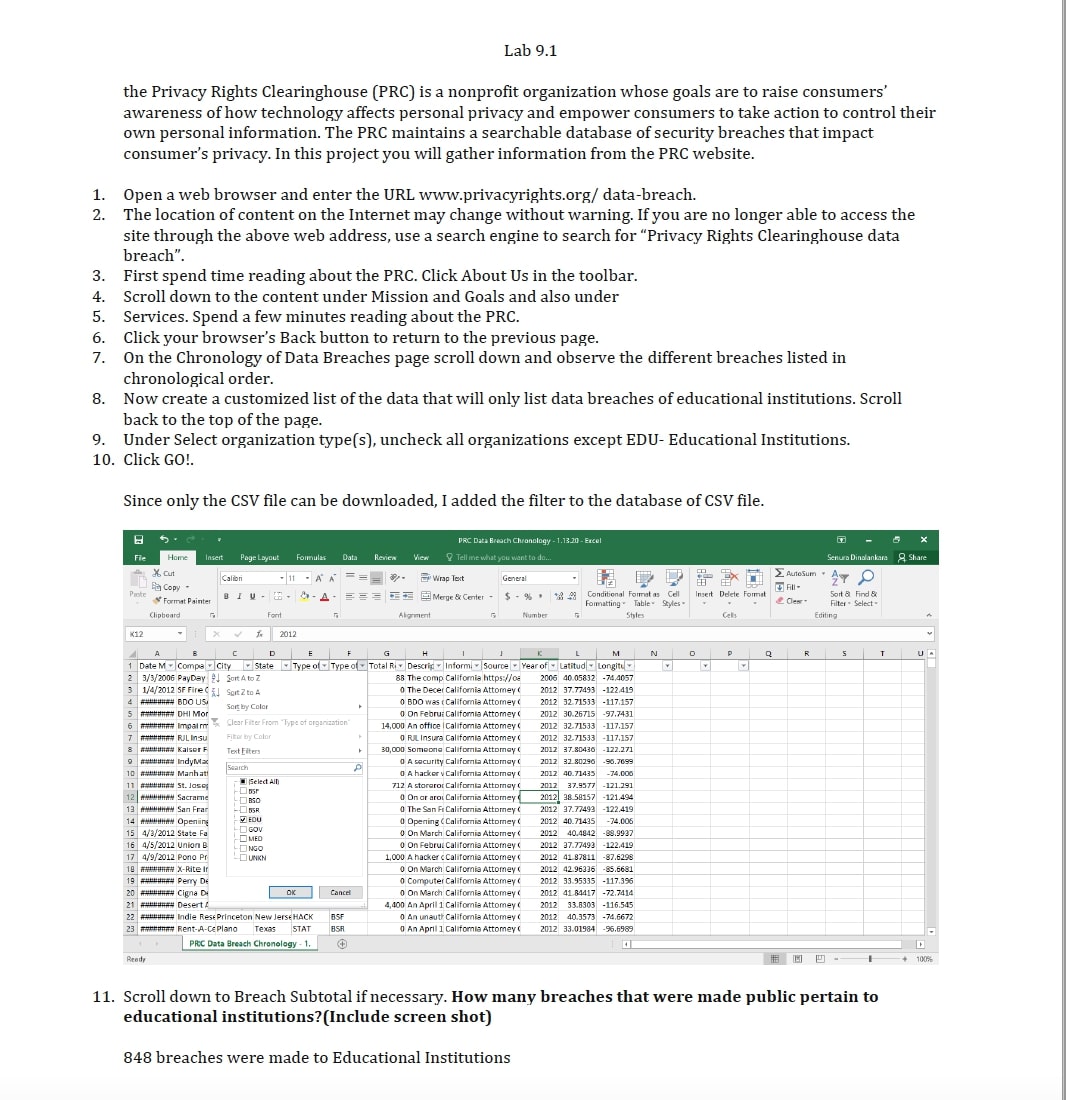
11. Scroll down to Breach Subtotal if necessary. How many breaches that were made public pertain to educational institutions?(Include screen shot)
12. Scroll down and observe the breaches for educational institutions.
13. Scroll back to the top of the page. Click New Search, located beneath the GO! button.
14. Now search for breaches that were a result of lost, discarded, or stolen equipment that belonged to the government and military. Under Choose the type of breaches to display, uncheck all types except Portable device (PORT) - Lost, discarded or stolen laptop, PDA, smartphone, portable memory device, CD, hard drive, data tape, etc.
15. Under Select organization type(s), uncheck all organizations except GOV – Government and Military.
16. Click GO!.
17. Scroll down to Breach Subtotal, if necessary. How many breaches that were made public pertain to this type? (Include screen shot)
18. Scroll down and observe the breaches for governmental institutions.
19. Scroll back to the top of the page.
20. Now create a search based on criteria that you are interested in, such as the Payment Card Fraud against Retail/Merchants during the current year. Take a screen shot.
21. When finished, close all windows.
Lab 9.2
In this project you will download and run the Microsoft Safety Scanner to determine if there is any malware on the computer.
1. Determine which system type of Windows you are running. Click Start, Control Panel, System and Security, and then System. Look under System type for the description.
2. Open your web browser and enter the URL www.microsoft.com/security/scanner/en-us/default.asp
3. Click Download Now.
4. Select either 32-bit or 64-bit, depending upon which system type of
5. Windows you are running.
6. When the program finishes downloading, right-click Start and click
7. Open Windows Explorer.
8. Click the Downloads icon in the left pane.
9. Double-click the msert.exe file.
10. Click Run. If the User Account Control dialog box appears, click Yes.
11. Click the check box to accept the license terms for this software. Click Next
12. Click Next.
13. Select Quick scan if necessary.
14. Click Next
15. Depending on your computer this scan may take several minutes. Analyze the results of the scan to determine if there is any malicious software found in your computer.
16. If you have problems you can click View detailed results of the scan. After reviewing the results, take screen shot and explain your results.
17. click OK.
18. If you do not find any problems, click Finish.
19. Run the scan again and select Full scan. After the scan is complete take screen shot. How many files were scanned? How many were infected?
20. click Finish to close the dialog box.
21. Close all windows.
Scan for Malware Using the Windows Defender
1. Search virus & threat protection
2. Click to start virus & threat protection
3. Click scan now
4. How many files were scanned? How many threats were found?
5. Take a screen shot.
6. Close Windows Defender
7. copy the string X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H* into a notepad and save it.
8. What happen to the file? Explain what just happened
9. Click the Virus and Threat protection Notification to see details
10. Close all windows
the Privacy Rights Clearinghouse (PRC) is a nonprofit organization whose goals are to raise consumers’ awareness of how technology affects personal privacy and empower consumers to take action to control their own personal information. The PRC maintains a searchable database of security breaches that impact consumer’s privacy. In this project you will gather information from the PRC website.
1. Open a web browser and enter the URL www.privacyrights.org/ data-breach.
2. The location of content on the Internet may change without warning. If you are no longer able to access the site through the above web address, use a search engine to search for “Privacy Rights Clearinghouse data breachâ€.
3. First spend time reading about the PRC. Click About Us in the toolbar.
4. Scroll down to the content under Mission and Goals and also under
5. Services. Spend a few minutes reading about the PRC.
6. Click your browser’s Back button to return to the previous page.
7. On the Chronology of Data Breaches page scroll down and observe the different breaches listed in chronological order.
8. Now create a customized list of the data that will only list data breaches of educational institutions. Scroll back to the top of the page.
9. Under Select organization type(s), uncheck all organizations except EDU- Educational Institutions.
10. Click GO!.
11. Scroll down to Breach Subtotal if necessary. How many breaches that were made public pertain to educational institutions?(Include screen shot)
12. Scroll down and observe the breaches for educational institutions.
13. Scroll back to the top of the page. Click New Search, located beneath the GO! button.
14. Now search for breaches that were a result of lost, discarded, or stolen equipment that belonged to the government and military. Under Choose the type of breaches to display, uncheck all types except Portable device (PORT) - Lost, discarded or stolen laptop, PDA, smartphone, portable memory device, CD, hard drive, data tape, etc.
15. Under Select organization type(s), uncheck all organizations except GOV – Government and Military.
16. Click GO!.
17. Scroll down to Breach Subtotal, if necessary. How many breaches that were made public pertain to this type? (Include screen shot)
18. Scroll down and observe the breaches for governmental institutions.
19. Scroll back to the top of the page.
20. Now create a search based on criteria that you are interested in, such as the Payment Card Fraud against Retail/Merchants during the current year. Take a screen shot.
21. When finished, close all windows.
Lab 9.2
In this project you will download and run the Microsoft Safety Scanner to determine if there is any malware on the computer.
1. Determine which system type of Windows you are running. Click Start, Control Panel, System and Security, and then System. Look under System type for the description.
2. Open your web browser and enter the URL www.microsoft.com/security/scanner/en-us/default.asp
3. Click Download Now.
4. Select either 32-bit or 64-bit, depending upon which system type of
5. Windows you are running.
6. When the program finishes downloading, right-click Start and click
7. Open Windows Explorer.
8. Click the Downloads icon in the left pane.
9. Double-click the msert.exe file.
10. Click Run. If the User Account Control dialog box appears, click Yes.
11. Click the check box to accept the license terms for this software. Click Next
12. Click Next.
13. Select Quick scan if necessary.
14. Click Next
15. Depending on your computer this scan may take several minutes. Analyze the results of the scan to determine if there is any malicious software found in your computer.
16. If you have problems you can click View detailed results of the scan. After reviewing the results, take screen shot and explain your results.
17. click OK.
18. If you do not find any problems, click Finish.
19. Run the scan again and select Full scan. After the scan is complete take screen shot. How many files were scanned? How many were infected?
20. click Finish to close the dialog box.
21. Close all windows.
Scan for Malware Using the Windows Defender
1. Search virus & threat protection
2. Click to start virus & threat protection
3. Click scan now
4. How many files were scanned? How many threats were found?
5. Take a screen shot.
6. Close Windows Defender
7. copy the string X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H* into a notepad and save it.
8. What happen to the file? Explain what just happened
9. Click the Virus and Threat protection Notification to see details
10. Close all windows
Solution Preview
These solutions may offer step-by-step problem-solving explanations or good writing examples that include modern styles of formatting and construction of bibliographies out of text citations and references.
Students may use these solutions for personal skill-building and practice.
Unethical use is strictly forbidden.
This is only a preview of the solution.
Please use the purchase button to see the entire solution.
Please use the purchase button to see the entire solution.
By purchasing this solution you'll be able to access the following files:
Solution1.pdf
Solution2.zip
Purchase Solution
$13.50







View Available
Computer Science Tutors 645 tutors matched
Ionut
(ionut)
Master of Computer Science
Hi! MSc Applied Informatics & Computer Science Engineer. Practical experience in many CS & IT branches.Research work & homework
5/5 (6,808+ sessions)
1 hour avg response
$15-$50 hourly rate
Pranay
(math1983)
Doctor of Philosophy (PhD)
Ph.D. in mathematics and working as an Assistant Professor in University. I can provide help in mathematics, statistics and allied areas.
4.6/5 (6,703+ sessions)
1 hour avg response
$40-$50 hourly rate
Leo
(Leo)
Doctor of Philosophy (PhD)
Hi!
I have been a professor in New York and taught in a math department and in an applied math department.
4.9/5 (6,469+ sessions)
2 hours avg response